One of the most dangerous types of malware is designed to gain remote access to a victim’s PC, such as Remote Access Trojans (RATs) and kernel-level rootkits. They operate silently, making detection difficult. If you are concerned whether someone has unauthorized remote access to your Windows PC, learn how to confirm and remove the threat.
Warning Signs of Someone Has Access to Your PC
While most remote access attempts are silent, they do come with some warning signs. While these signs could be seen as common Windows problems, combined, they can be solid proof of remote access activity.
- Unusual mouse/keyboard activity: if your cursor moves erratically or text is typed without your input, it could be the work of a remote tool. Even when not actively controlling, these tools can cause issues like the cursor jumping/teleporting around. This sign can also work as a confirmation if the mouse and keyboard start executing tasks like accessing the browser address bar and entering a website address.
- Programs opening and closing on their own: a hacker could also send commands to open specific apps (like antivirus or the Command Prompt) to control the system further or disable security functions. If you notice programs opening and closing on their own, it’s a red flag.
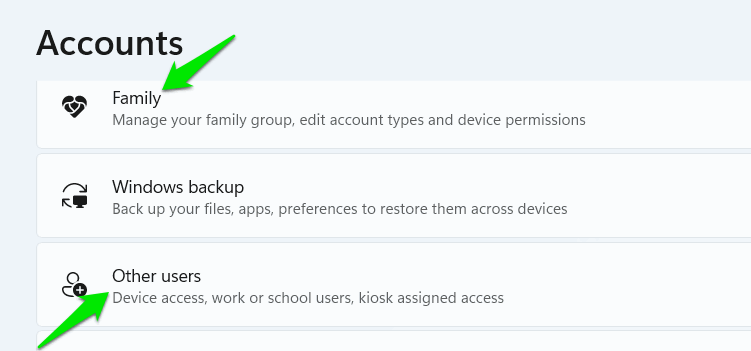
- Creation of new unknown user accounts: some bad actors may try to create secondary accounts to have persistent access even after detection. They will probably disable user switching to hide the accounts from the lock screen. Go to Windows Settings -> Accounts, and look for secondary accounts in the Family and Other users sections.
- Sudden slow performance: remote control activity also consumes a lot of resources, so you may notice a sudden drop in performance. This is especially worth considering if performance drops arise occasionally because of remote control activity.
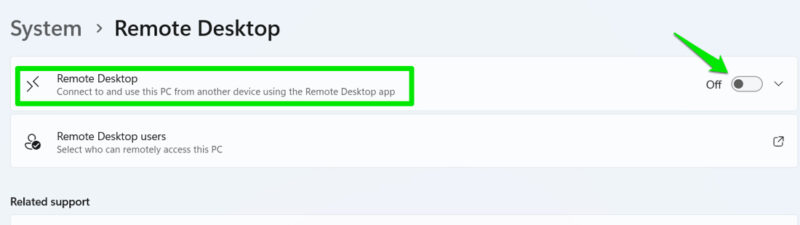
- Windows remote desktop is enabled on its own: Windows remote desktop is quite vulnerable, so hackers often use it to create a remote connection. It’s disabled by default, so if it’s turned on without your intervention, it could be a hacker’s doing. In Windows Settings, go to System -> Remote Desktop and see if it’s been enabled.
How to Confirm Your PC Is Being Accessed Remotely
If you notice the above signs, take the necessary steps to confirm the suspicion. You can track the activity of components/apps involved in the remote access process to confirm someone is accessing your Windows PC. The following are some of the most reliable methods:
Check Windows Event Viewer logs
Windows Event Viewer is a great built-in tool to track user activity and help detect remote access attempts by tracking RDP activity and login logs.
Search for “event viewer” in Windows Search, and open the Event Viewer.
Move to Windows Logs -> Security, and click on the Event ID tab to sort events by ID. Look for all events with ID 4624, and check their details to ensure there are no events with Logon Type 10. Event ID 4624 is for logon attempts, and Logon Type 10 corresponds to remote logons using remote access services, which hackers may use.
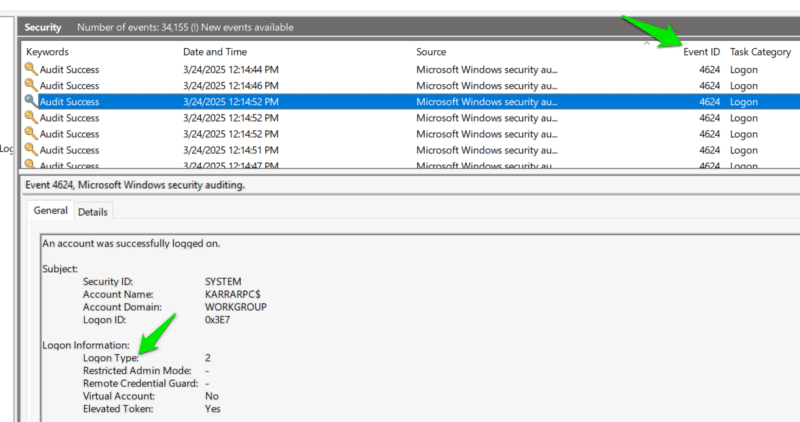
You can also look for Event ID 4778, as it shows remote session reconnection. The details page of each event will tell you important identification details, like account name or network IP address.
Track network traffic
Remote access depends on the network connection, so tracking the network traffic is a reliable way to detect it. We recommend using the GlassWire free version for this, as it both helps track and automatically defend against malicious connections.
In the GlassWire app, you’ll see all app connections under the GlassWire Protect section. The app will automatically rate the connections and flag untrustworthy connections. In most cases, it should be able to detect malicious remote connections and warn you.
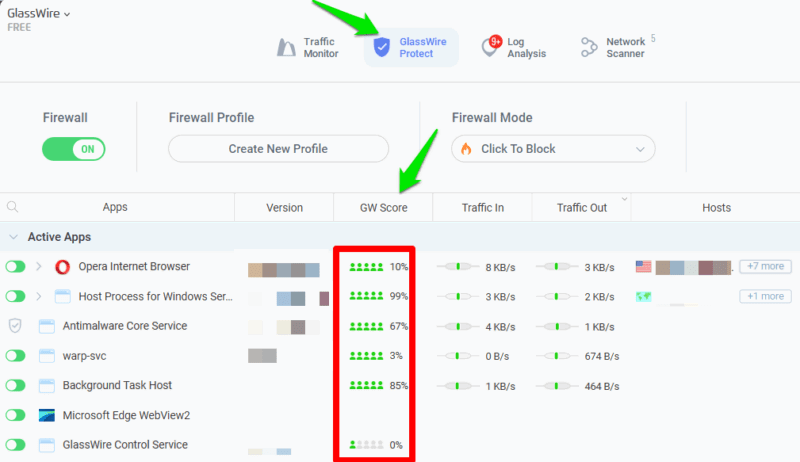
Beyond the app’s algorithms, you can also look for clues like high data usage of an unknown app. Remote connection uses continuous data, so it should be easy to detect.
Look at scheduled tasks
Many remote access attempts are managed using the Task Scheduler tool in Windows. This helps them persist through PC restarts and execute tasks without needing to run continuously. If your PC is infected, you should see tasks from unknown apps in the Task Scheduler.
Search for “task scheduler” in Windows Search, and open the Task Scheduler app. In the panel on the left, open Task Scheduler (Local) -> Task Scheduler Library. Look for any unfamiliar or suspicious folder other than Microsoft. If you find any, right-click on the task and select Properties.
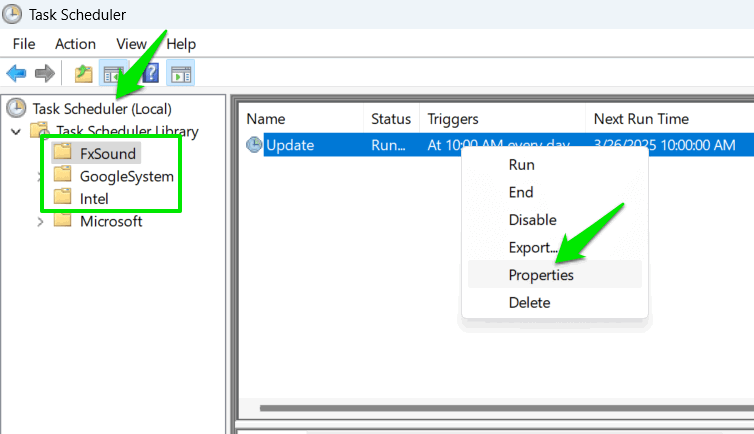
In Properties, look through the Triggers and Actions tabs to learn what the task does and when it executes, which should be enough to understand whether it’s bad. For example, if the task runs an unknown app or script at logon or when the system is idle, it could be for malicious purposes.
If you do not find suspicious tasks, you may want to take a look at the Microsoft folder. There is a possibility that sophisticated malware is hiding in the system folders. Look for tasks that seem suspicious, such as having generic names like “systemMonitor” or misspelled names. Thankfully, you won’t have to research each task, as most will have the author as Microsoft Corporation, which are safe to skip.
How to Stop Remote Access and Secure Your PC
Once you’ve confirmed that someone has remote access to your Windows PC, your first step should be disconnecting from the internet so that they can’t do further damage. Your priority should be damage control rather than getting rid of the threat. Therefore, use another device to reset passwords of important accounts, like email, financial accounts, social media accounts, etc. Also, ensure that you back up important data.
Follow the below methods to get rid of the remote access malware:
Run Microsoft Defender offline scan
If your security system is unable to detect or protect against this remote access attack, it could be advanced malware, like rootkits or bootkits. Microsoft Defender’s offline scan could help you. It will scan your PC during the startup in a secure and minimal environment to find malware when it is inactive.
To run the scan, search for “windows security” in Windows Search, and open the Windows Security app.
Go to Virus & threat protection -> Scan options, select Microsoft Defender Antivirus (offline scan), and click Scan now.
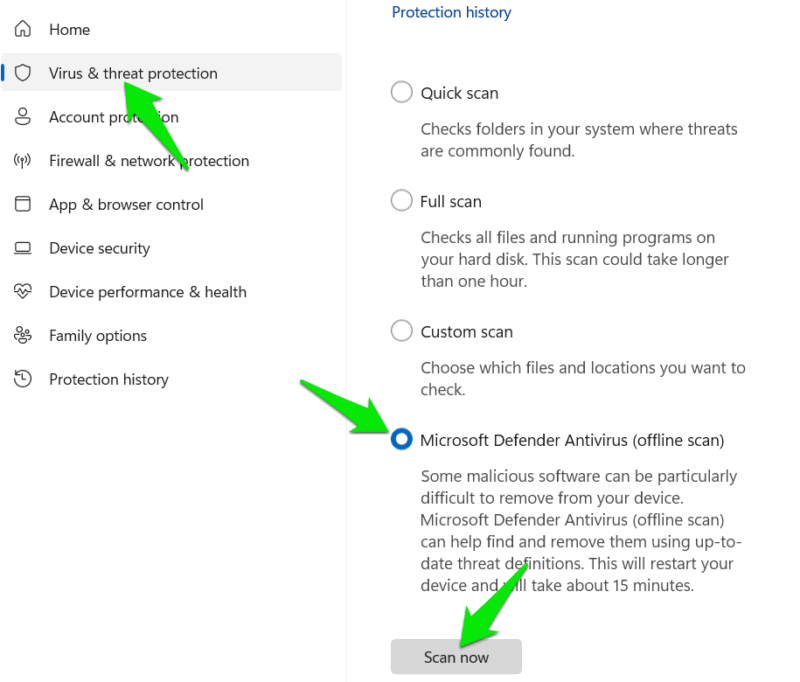
This will restart your PC and run a full system scan. If any threats are found, they will be in the Protection history section of the Windows Security app.
Get rid of suspicious programs
Whether the scan detects something or not, you should do a manual audit of programs to make sure you don’t have an unknown program acting as a gateway. In Windows Settings, go to Apps -> Installed apps, and look for any apps that aren’t part of Windows and that you don’t remember installing. Furthermore, get rid of remote access apps that could be compromised, like TeamViewer, AnyDesk, VNC, Chrome Remote Desktop, etc.
There is a possibility that a malicious browser extension is the cause. Make sure you check all extensions and uninstall shady extensions.
Block inbound remote access ports in firewall
If you don’t remotely access your PC or receive assistance from anyone, you can block common inbound ports for remote connections in the firewall. This blocks incoming remote connections but allows you to control other devices if needed.
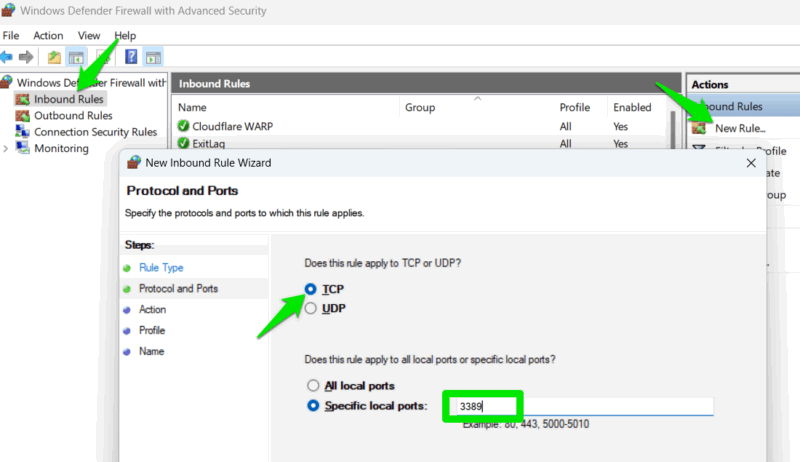
Search for “windows defender firewall” in Windows Search, and open the Windows Defender Firewall with Advanced Security app.
Select Inbound Rules -> New Rule, then Port -> Next. Select TCP and provide one of the port numbers listed below.
- 3389 (Windows Remote Desktop)
- 5900 (Virtual Network Computing)
- 5938 (TeamViewer)
- 6568 (AnyDesk)
- 8200 (GoToMyPC)
Select Block the connection, and complete the setup to create the rules. Make sure you give a clear name to the rule so that you can identify it later. Repeat this process for each port to block it.
Do a clean Windows install if needed
If nothing is working, or you don’t want to take any chances, doing a clean Windows install is another option. It’s extremely rare for malware to survive both an offline antivirus scan and a clean OS install. However, you’ll have to back up your important data, as a clean install will delete all the data on your PC.
Check out our guide on how to perform a clean install of Windows to learn all the steps to safely install a clean Windows.
Never take chances if you are suspicious about PC access, whether it’s remote access or local access. Such control always escalates to bigger security issues. Of course, it’s best to prevent it from happening in the first place, so make sure you use these Windows security settings and advanced Windows Defender options.
Image credit: Vecteezy. All screenshots by Karrar Haider.